Setting Up Amazon RDS MariaDb Server
Note
The Persephone system is now supplied in a form of a single Docker image. Once the Docker image is installed, you can start using PersephoneShell to populate the data and run the Persephone application. Please refer to this page.
The text below and the following pages are provided here for those who want to install (and configure) the Persephone components separately, without using Docker.
This section provides the steps to set up a MySQL-compatible (MariaDb) server on an Amazon Web Services (AWS) Relational Database Service (RDS). Persephone will work with MySQL-compatible databases, but we highly recommend using MariaDb - in our tests, it appears much more reliable and faster than MySQL.
- Open an AWS account with an AWS master account named, for example, "AWSME".
Tip
You can sign up for an Amazon AWS account by navigating to https://portal.aws.amazon.com/gp/aws/developer/registration/index.html and then follow the directions on the screen.
- Login to AWS as the master user AWSME and create an AWS Identity and Access Management (IAM) user account named, for example, "PERSEPHONE".
Tip
Refer to Amazon's "To create an IAM user for yourself" section on the Creating an Administrators Group Using the Console page for more information.
- Before creating the database instance, we need to have a Parameter group with variables set to the required values listed below.
You can find the corresponding link in the list on the left of the RDS console: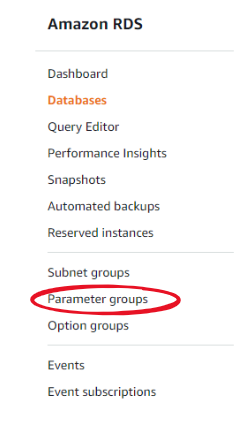
- Create a new group and edit its parameters to have the following values (all are required for normal operation).
character_set_database='utf8'
character_set_server='utf8'
lower_case_table_names=1
log_bin_trust_function_creators=1
net_write_timeout=3600
net_read_timeout=3600
You can use "Filter parameters" search box to find the needed parameter: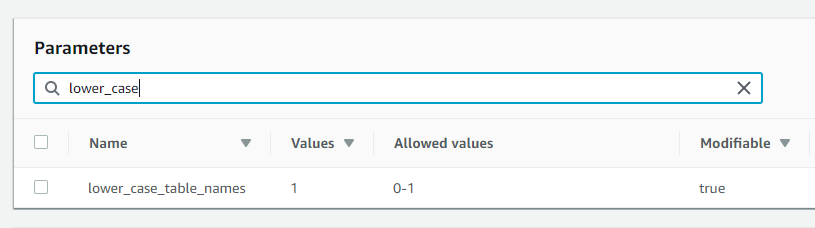
- Create a MariaDb (not higher than version 10.11.*) RDS database named, for example, "PERSDB" (with sufficient storage space and processing power) with IAM user PERSEPHONE as the master user. Please ensure that you are using the newly created Parameter group.
An instance class db.m4.xlarge and the following configuration for a database with a few users proved to be sufficient:
|
Parameter |
Value |
|
vCPU |
4 |
|
RAM |
16 GB |
|
Multi AZ |
No ("Yes" will double the cost) |
|
Storage type |
Provisioned IOPS (SSD) |
|
IOPS |
1000 |
|
Storage |
1000 GiB |
In the case you want to maintain the database with users connecting to it from the computers outside of Amazon Virtual Private Cloud (VPC), you will have to set "Public accessibility" to ON and limit the connections via security groups that can control which IPs are allowed to connect. If all the database administration will be done within the VPC, set "Public accessibility" to OFF.
To allow certain IPs to connect, create a security group and modify its Inbound rules, normally, to MySQL port 3306. One of such IPs will belong to the API-server Cerberus that will be residing inside the VPC on one of the AWS EC2 instances, so we can use its internal IP (see Cerberus).
Please note the database Endpoint that is shown under Connectivity & security tab - we will need it to specify the connection string:
- The rest of the set up process is common for an Amazon RDS-based or a local MariaDb instance and is described here.
- For your reference, here is the summary of parameters that might improve the database performance:
|
Parameter |
Value |
|
character_set_server |
utf8 |
|
innodb_log_file_size |
268435456 |
|
innodb_strict_mode |
1 |
|
join_buffer_size |
1048576 |
|
log_bin_trust_function_creators |
1 |
|
long_query_time |
1 |
|
lower_case_table_names |
1 |
|
max_allowed_packet |
67108864 |
|
max_connections |
400 |
|
max_heap_table_size |
16777216 |
|
slow_query_log |
1 |
|
sql_mode |
STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION,NO_AUTO_VALUE_ON_ZERO,ERROR_FOR_DIVISION_BY_ZERO,ONLY_FULL_GROUP_BY |
|
tmp_table_size |
16777216 |
|
tx_isolation |
READ-COMMITTED |
|
net_write_timeout |
3600 |
|
net_read_timeout |
3600 |
